 Around the world, not just in the United States, there has been a lot of evidence of the Russian government’s involvement, directly or indirectly, in elections. This week, Microsoft announced their Digital Crimes Unit successfully executed a court order to disrupt and transfer control of 6 domain names created by a group widely associated with the Russian government and known as Strontium, or alternatively Fancy Bear or APT28.
Around the world, not just in the United States, there has been a lot of evidence of the Russian government’s involvement, directly or indirectly, in elections. This week, Microsoft announced their Digital Crimes Unit successfully executed a court order to disrupt and transfer control of 6 domain names created by a group widely associated with the Russian government and known as Strontium, or alternatively Fancy Bear or APT28.
In a post by their own President, Brad Smith, on the Microsoft blog, Smith writes how Microsoft has “now used this approach 12 times in two years to shut down 84 fake websites associated with this group. Attackers want their attacks to look as realistic as possible and they therefore create websites and URLs that look like sites their targeted victims would expect to receive email from or visit. The sites involved in last week’s order fit this description.”
Last week’s order transferred control of the 6 domain names listed below from Strontium to Microsoft, preventing Strontium from using them and enabling Microsoft to more closely look for evidence of what Strontium intended to do with the domains. The 6 domains are:
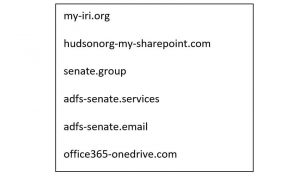
Microsoft note that these domain names show a broadening of entities targeted by Strontium’s activities. One appears to mimic the domain name of the International Republican Institute, which promotes democratic principles and is led by a notable board of directors, including 6 Republican senators and a leading senatorial candidate. Another is similar to the domain used by the Hudson Institute, which hosts prominent discussions on topics including cybersecurity, among other important activities. Other domains appear to reference the U.S. Senate but are not specific to particular offices. Microsoft makes it clear that they currently have no evidence these domains were used in any successful attacks before the DCU transferred control of them, nor do they have evidence to indicate the identity of the ultimate targets of any planned attack involving these domains.
Despite last week’s steps, we are concerned by the continued activity targeting these and other sites and directed toward elected officials, politicians, political groups and think tanks across the political spectrum in the United States. Taken together, this pattern mirrors the type of activity we saw prior to the 2016 election in the United States and the 2017 election in France.
Microsoft is concerned that these and other attempts pose security threats to a broadening array of groups connected with both American political parties in the run-up to the 2018 elections. So this week Microsoft announced they are expanding their Defending Democracy Program with a new initiative called Microsoft AccountGuard. This initiative will provide state-of-the-art cybersecurity protection at no extra cost to all candidates and campaign offices at the federal, state and local level, as well as think tanks and political organizations we now believe are under attack. The technology is free of charge to candidates, campaigns and related political institutions using Office 365.
As a special master appointed by a federal judge concluded in the recent court order obtained by DCU, there is “good cause” to believe that Strontium is “likely to continue” its conduct. In the face of this continuing activity, we must work on the assumption that these attacks will broaden further. An effective response will require even more work to bring people and expertise together from across governments, political parties, campaigns and the tech sector.
This latest Domain News has been posted from here: Source Link
