The latest Akamai State of the Internet report focuses on phishing
and includes how short-lived domain names play their part. Phishing is a huge
cost to brands large and small, and even individuals. Ever escalating defences
against phishing are being met with ever escalating efforts by criminals with phishing
having “evolved from being an email-based attack to one that now includes
mobile devices and social media. This evolution is leveraging the world’s
increasingly connected existence as a means of rapid propagation. This means
that criminals now have more options when it comes to targeting their victims.”

In their report, Akamai explain “Phishing attacks require
two things: a lure and a landing. There are times when the lure is also the
landing, so the technical elements of an attack depend on the phishing campaign
itself, the scope, and the targets.”
“A lure gets the victim’s attention, by way of a warning, an urgent request, or some other message invoking a sense of alarm or concern. Once the lure works, the victim needs to land, and that is where the final phase of the attack happens.”
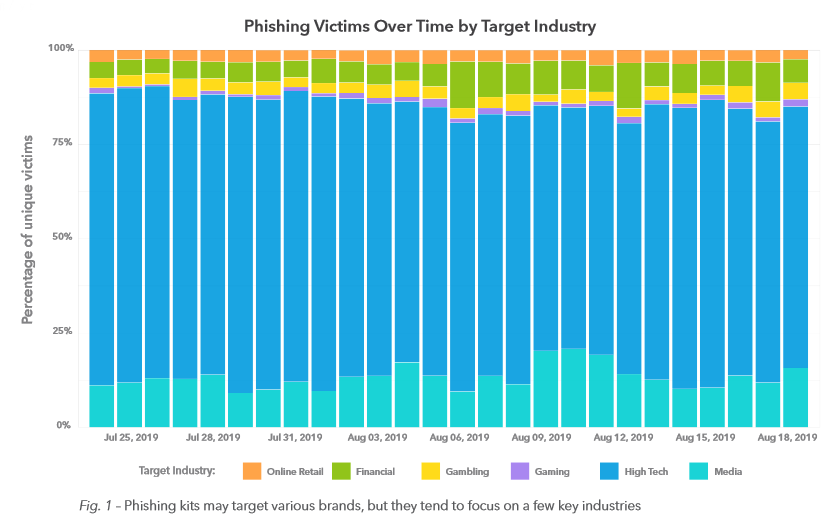
“The landing can be anything, including malicious
attachments or links, a perfect clone of a bank’s website, a retail portal, or
a simple form requesting information in exchange for some type of prize or
reward.”
“Most landing elements in any given phishing attack involve
a platform, better known as a kit. For this report we’ll focus on phishing
kits. As a whole, phishing kits are anything but consistent.”
There are 2 types of phishing: generic phishing attacks, of which botnets are part, which are a numbers game where the criminal blasts their lure out to thousands — sometimes tens of thousands — of potential victims; and spear phishing attacks that usually only target one person or a group (such as a retailer’s customer base or a group of activists). Sometimes spear phishing attacks target a whole company and are mistaken for generic phishing attacks at first. What sets them apart from generic attempts, however, are the granular details. Spear phishing is commonly seen in nation-state attacks, corporate espionage campaigns, and fraudulent financial attacks in which the ultimate goal isn’t basic information gathering, but something more destructive or consequential.
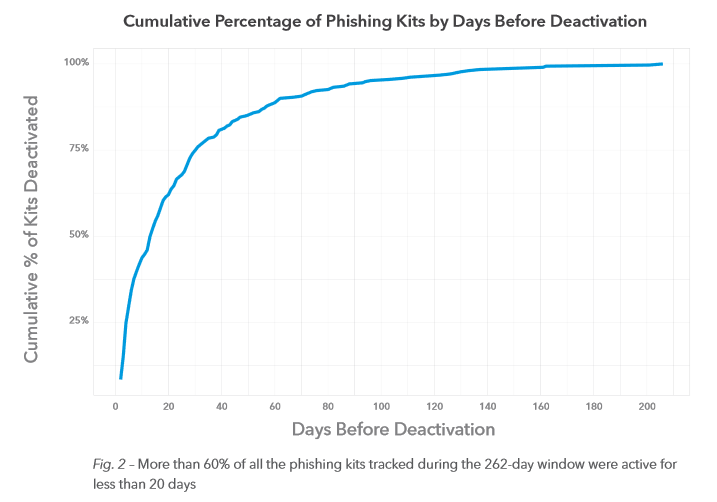
And here’s where domain names come into phishing. The report
explains “sometimes phishing kits are uploaded to a compromised website. When
this happens, the attacker has exploited a vulnerability in the website’s CMS
or on the server itself. Hijacking a domain like this to host a phishing kit
takes advantage of the URL’s positive reputation and age, which enables the
attacker to remain hidden longer. In other instances, the criminal will choose
to purchase a domain and hosting package of their own.”
The report notes how “age is important when phishing URLs
are considered. Newly created domains — those that are less than a month old —
are often flagged as suspicious by security products.”
Explaining how criminals take advantage of short-lived domains,
researchers track domain registrations and report domains frequently if they
raise any red flags. The criminals take advantage of top-level domain (TLD)
sales at a given registrar, buying in bulk and rotating through their
collection during a given phishing run. This allows them to keep operating even
if one of their domains — or several of them — are taken down or flagged.
The financial benefits can be significant. The report notes
how “in instances like these, a domain that lasts for a few days could yield
hundreds of victims, but even those that only last a few hours still return net
positive results to the criminal. This is because after the initial outlay of
expenses (domains, phishing kits, and perhaps hosting), a criminal only needs a
few victims to get their money back. Everything after that is pure profit.”
There’s a race that goes on between the criminals and
security teams looking to shut down their operations. “Although security teams
report phishing URLs regularly, some criminals choose web hosts and domains
where those reports are simply ignored. Yet, as the data shows, most kits have
a short life, and the window of opportunity for most phishing kits is growing
smaller.”
“Over a 60-day period, Akamai observed more than 2,064,053,300 unique domains commonly associated with malicious activity. Of those, 89% had a lifespan of less than 24 hours, and 94% had a lifespan of less than three days.”
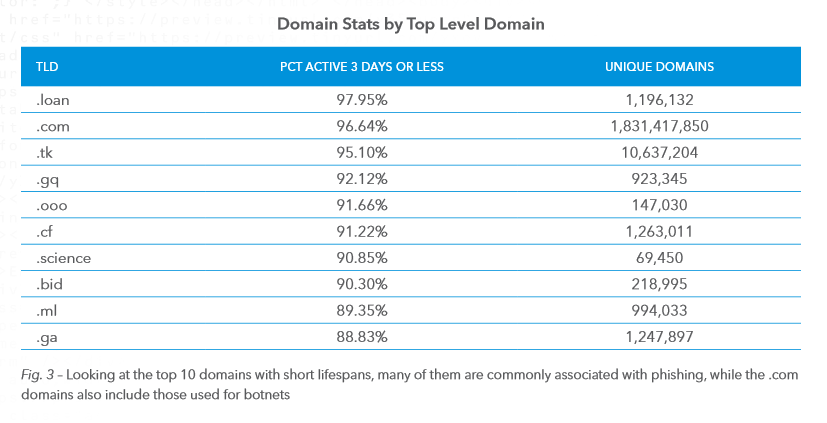
“Considering the phishing domains, notable short-lived TLDs
such as .gq, .loan, and .tk have a median lifespan of 24 hours and mean
lifespan of less than two days. Looking at the data, the availability of cheap
name registration on TLDs such as these is a boon to criminals; it makes
detection more difficult because the names live in traffic so briefly.
“The high number of .com domains with short lifespans can be
attributed to names used for botnet traffic, with large numbers of new names
used daily (most of which are not registered and so do not resolve).”
To download the Akamai State Of The Internet report called Phishing — Baiting the Hook, see: akamai.com/us/en/multimedia/documents/state-of-the-internet/soti-security-phishing-baiting-the-hook-report-2019.pdf
This latest Domain News has been posted from here: Source Link
